While traveling through Dulles Airport last week, I noticed an Internet oddity. The nearby AT&T hotspot was fairly fast—that was a pleasant surprise.
But the web had sprouted ads. Lots of them, in places they didn’t belong.
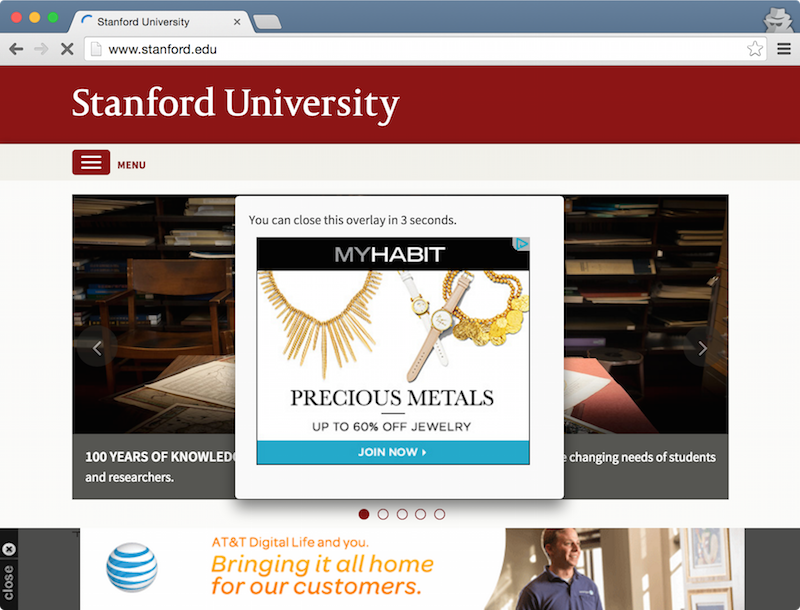
Last I checked, Stanford doesn’t hawk fashion accessories or telecom service.1 And it definitely doesn’t run obnoxious ads that compel you to wait.
Some ad-supported websites, like the Wall Street Journal, were also emblazoned with extra marketing material.
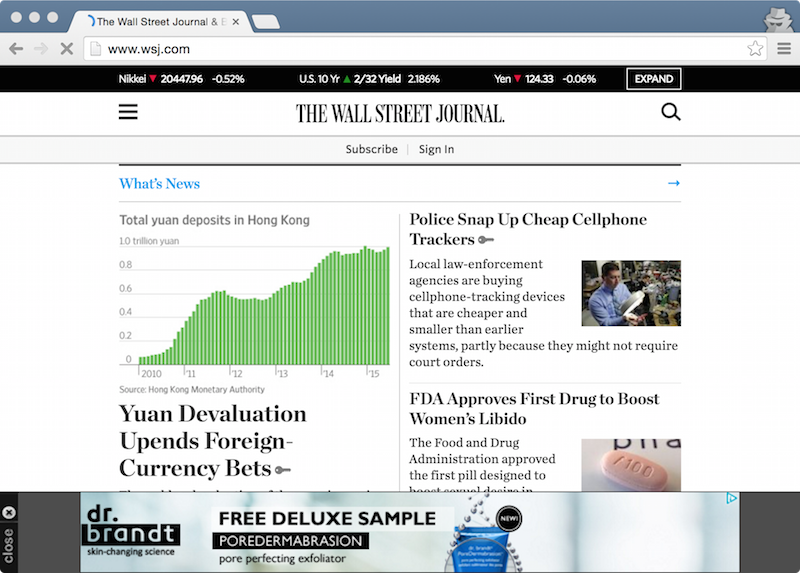
Same goes for certain federal government websites.

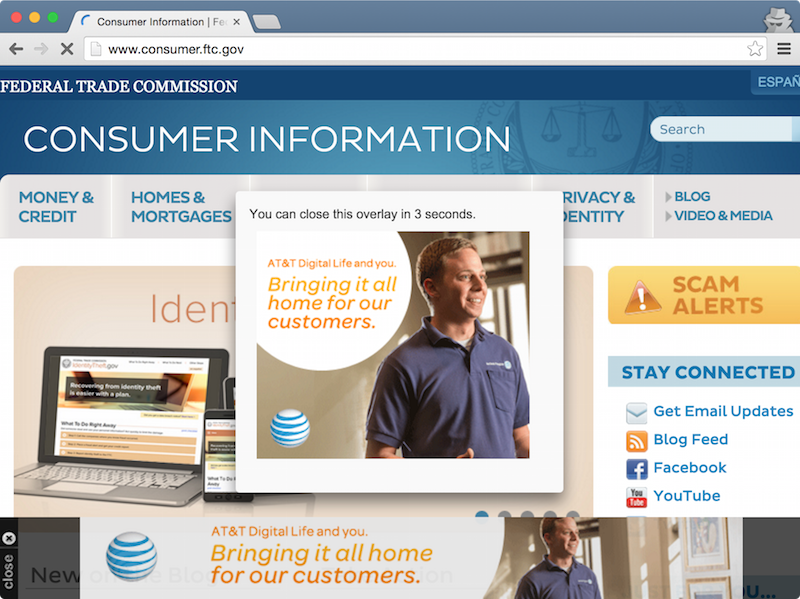
Curious, and waiting on a delayed flight, I started poking through web source. It took little time to spot the culprit: AT&T’s wifi hotspot was tampering with HTTP traffic.
The ad injection platform appears to be a service from RaGaPa, a small startup. Their video pitch features “MONETIZE YOUR NETWORK” over cascading dollar signs. (Seriously.)
When an HTML page loads over HTTP, the hotspot makes three edits. (HTTPS traffic is immune, since it’s end-to-end secure.)
First, the hotspot adds an advertising stylesheet.
<head><link rel="stylesheet" type="text/css" href="http://adapi.ragapa.com/v1/rgp-location-layout-css?id=att-rrna-07252015">
Next, it injects a backup advertisement, in case a browser doesn’t support JavaScript. It appears that the hotspot intercepts /ragapa URLs and resolves them to advertising images.2
<body><noscript><div id='ragapatop' name='ragapatop'><img src='/ragapa?ragapanoscript=2811' height='65px' /></div></noscript>
Finally, the hotspot adds a pair of scripts for controlling advertisement loading and display.
<script type="text/javascript" src="http://adapi.ragapa.com/v1/rgp-location-layout-html?id=att-rrna-07252015"></script><script type="text/javascript" src="http://adapi.ragapa.com/v1/rgp-location-layout?id=att-rrna-07252015"></script></body> </html>
Those scripts, in turn, import advertising content from additional third-party providers.
AT&T has an (understandable) incentive to seek consumer-side income from its free wifi service, but this model of advertising injection is particularly unsavory. Among other drawbacks: It exposes much of the user’s browsing activity to an undisclosed and untrusted business. It clutters the user’s web browsing experience. It tarnishes carefully crafted online brands and content, especially because the ads are not clearly marked as part of the hotspot service.3 And it introduces security and breakage risks, since website developers generally don’t plan for extra scripts and layout elements.
Recent experience with advertisement injection is telling. When a Marriott property was spotted deploying similar technology, it immediately reversed course. The handful of U.S. ISPs that have dabbled in advertising injection appear to have backed off. Earlier this year, Google conducted a comprehensive study of advertising injection, and yanked nearly 200 misleading extensions from the Chrome Web Store. The closest common practice, to my knowledge, is injecting hotspot status indicators—and that’s also proven extraordinarily controversial.
The legality of hotspot advertising injection is a messy subject. There are a number of colorable arguments against, including under the FCC’s net neutrality rules,4 the FTC’s unfairness and deception authorities (and state parallels),5 wiretapping statutes,6 pen register statutes, tortious interference, copyright, and more. It certainly doesn’t help AT&T and RaGaPa that the ads aren’t labeled as associated with the hotspot, and that AT&T’s wifi terms of service are silent about advertising injection.7
Regardless of where the law is, AT&T should immediately stop this practice. And if websites needed (yet another) reason to adopt HTTPS, here’s a good one.
I write shorter stuff at @jonathanmayer.
1. Since I imagine some readers will be pedantic—yes, the Stanford bookstore does sell a small selection of jewelry, and yes, Stanford does provide on-campus Internet service.
2. I didn’t have time to test this feature before I boarded my flight. It seems a particularly poor technical design, since it relies on avoiding URL path collisions and it misrepresents the source of content.
3. While the most frequent advertisements appeared to be related to AT&T services, they were ordinary banner ads for residential offerings, not marked in any way as associated with the hotspot. And, at any rate, many ads had nothing to do with AT&T.
4. In precise regulatory terminology, AT&T’s hotspot network is (arguably) a “broadband Internet access service,” and is (also arguably) “unreasonably interfering with” or “unreasonably disadvantaging” consumer or website connectivity.
5. The FTC’s ability to enforce against AT&T depends on the FCC’s net neutrality rules. If the free component of AT&T’s hotspot network is a covered “broadband Internet access service,” then the FTC Act’s common carrier exception prevents enforcement. The FTC could still bring an action against RaGaPa.
6. According to RaGaPa’s product sheet, one possible configuration involves redirecting all user traffic through RaGaPa’s servers. That would raise particularly thorny wiretapping issues. I didn’t spot the provision until after departing Dulles, unfortunately, so I didn’t test whether AT&T was re-routing customer traffic.
7. The closest passage in AT&T’s wifi terms of service is:
We may also enable certain technologies intended to improve your experience, maintain network security, and/or optimize network utilization that may generate records regarding the websites you visit and search terms you enter while using the Service.
AT&T might argue that ad injection “improve[s] your experience.” Good luck with that.